In today’s digital age, the security of your organization’s data and systems is more critical than ever. Cyber threats are evolving at an unprecedented pace, making it essential for businesses to stay ahead of potential risks. One of the most effective ways to do this is through a cyber threat risk assessment. But what exactly is a cyber threat risk assessment, and why is it so important?
What is a Cyber Threat Risk Assessment?
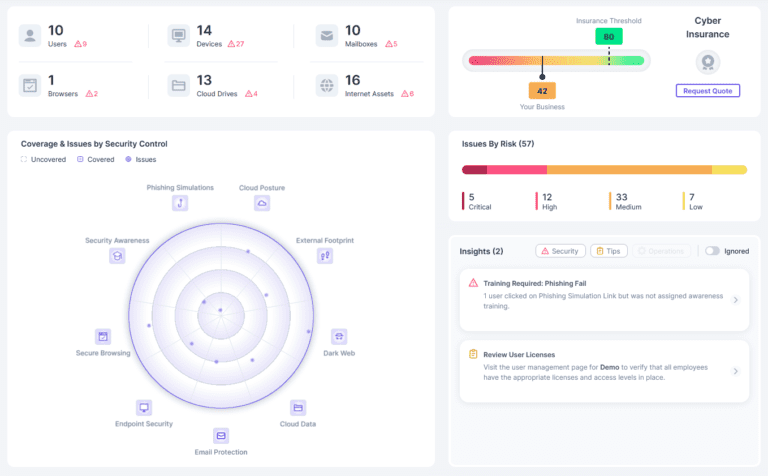
A cyber threat risk assessment is a systematic process used to identify, evaluate, and prioritize potential threats to an organization’s information systems. The goal is to understand the vulnerabilities within your network, assess the potential impact of different types of cyber attacks, and develop strategies to mitigate those risks. This proactive approach helps organizations safeguard their critical assets and maintain business continuity.
Key Components of a Cyber Threat Risk Assessment
- Comprehensive System Audits:
- Detailed analysis of your network, systems, and applications to identify potential vulnerabilities.
- Regular assessments to ensure up-to-date protection against evolving threats.
- Threat Landscape Analysis:
- Evaluation of current and emerging threats relevant to your industry and business operations.
- Strategic insights to prioritize and address the most significant risks.
- Vulnerability Scanning:
- Automated scanning tools to detect weaknesses in your IT infrastructure.
- Immediate alerts and reports to facilitate prompt remediation.
- Penetration Testing:
- Simulated cyber attacks to test the effectiveness of your security measures.
- Identifying exploitable vulnerabilities before malicious actors can find them.
- Risk Prioritization:
- Assessing the potential impact and likelihood of identified threats.
- Developing a prioritized action plan to address the most critical risks first.
- Security Policy Review:
- Evaluation of existing security policies and procedures.
- Recommendations for improvements to strengthen your overall security posture.
- Compliance Assessment:
- Ensuring your organization meets industry standards and regulatory requirements.
- Identifying gaps and providing guidance to achieve full compliance.
- Incident Response Planning:
- Preparing a robust incident response plan to swiftly address and mitigate breaches.
- Regularly updating and testing the plan to ensure effectiveness during an actual incident.
Why is a Cyber Threat Risk Assessment Important?
- Proactive Risk Management: By identifying and addressing vulnerabilities before they can be exploited, organizations can significantly reduce the likelihood of a successful cyber attack.
- Regulatory Compliance: Many industries are subject to stringent regulatory requirements regarding data protection. Regular risk assessments help ensure compliance and avoid costly fines.
- Enhanced Security Posture: A thorough understanding of potential threats and vulnerabilities enables organizations to implement stronger security measures and policies.
- Business Continuity: By mitigating risks and preparing for potential incidents, organizations can minimize disruptions and maintain operations even in the face of cyber threats.
- Cost Savings: Investing in proactive risk assessments can save organizations significant amounts of money by preventing data breaches and the associated costs of remediation, legal fees, and reputation damage.
Sign up for our free “Why You Need a Cyber Threat Risk Assessment” training today and ensure your team is equipped to handle potential cyber threats. This free training offers real-world examples of common threats and practical strategies to mitigate them, providing your organization with the knowledge and tools needed to stay secure in an ever-changing cybersecurity landscape. No Spam, No Mailing list, It’s Free.