Why Cybersecurity is Crucial for Your Business
In today’s world, where almost everything is connected to the internet, protecting your business from cyber threats is essential. Hackers and cybercriminals are constantly finding new ways to steal data, money, and disrupt operations. At MDRDESK, we offer a range of services to keep your business safe online. Our goal is to make sure your information, systems, and networks are secure, so you can focus on running your business without worrying about cyber threats.
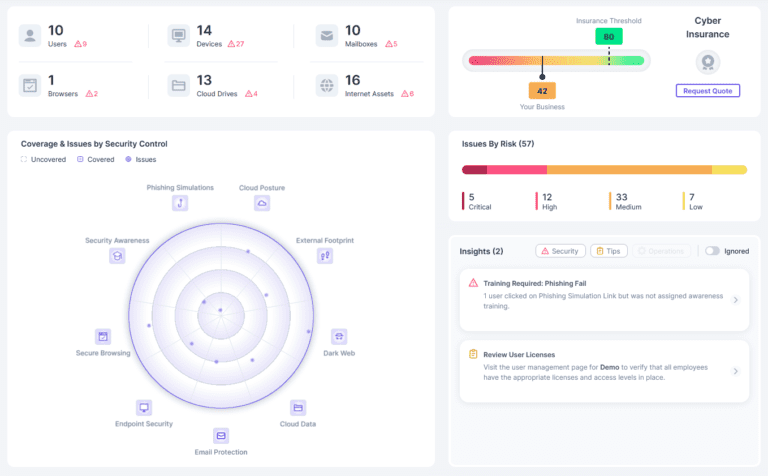
External Footprint Monitoring
What It Is: We check all the ways people can see your business online, such as websites and public profiles, to find any weak spots.
Why It’s Important: Hackers look for these weak spots to break into your systems. By identifying them first, we can fix them and keep your business safe.
Service Features:
- Regularly checking for open doors in your online presence.
- Looking for any information that shouldn’t be public.
- Keeping an eye out for potential threats.
Dark Web Monitoring
What It Is: We keep an eye on the dark web, a hidden part of the internet where stolen data is often sold, to see if your information is there.
Why It’s Important: If your data ends up on the dark web, it means hackers could use it to attack your business. By knowing early, we can help you protect yourself.
Service Features:
- Alerting you if your information is found.
- Monitoring for leaked passwords and other sensitive data.
- Helping you take quick action to protect your business.
Directory Posture Management
What It Is: We make sure that your systems, which control who can access what information, are set up correctly and securely.
Why It’s Important: If these systems are not set up properly, unauthorized people could access sensitive information. We ensure everything is configured securely.
Service Features:
- Scanning your systems for potential issues.
- Providing recommendations to improve security.
- Enforcing security policies to keep everything safe.
Secure Browsing
What It Is: We protect your internet browsing to prevent you from accidentally visiting dangerous websites.
Why It’s Important: Some websites are designed to harm your systems or steal information. Secure browsing helps avoid these sites and keeps your business safe.
Service Features:
- Blocking harmful websites in real-time.
- Ensuring safe internet use for all employees.
- Monitoring web activities to prevent threats.
Cloud Data Protection
What It Is: We protect your data stored in cloud services, like online storage and applications, from unauthorized access.
Why It’s Important: As more businesses use cloud services, protecting this data is crucial to prevent breaches and keep information secure.
Service Features:
- Regularly checking cloud environments for security issues.
- Enforcing security policies in the cloud.
- Protecting against data leaks and misconfigurations.
Managed Endpoint Protection
What It Is: We protect all your devices, including computers, laptops, and phones, from cyber threats.
Why It’s Important: Devices are often targeted by viruses and malware. Protecting these devices ensures your entire network remains secure.
Service Features:
- Continuously monitoring devices for security threats.
- Detecting and responding to any issues quickly.
- Managing security tools for all your devices.
Email Protection
What It Is: We secure your email to prevent phishing attacks, spam, and harmful attachments.
Why It’s Important: Emails are a common way for cybercriminals to attack businesses. Protecting your email helps prevent data theft and other cyber threats.
Service Features:
- Advanced filtering to block harmful emails.
- Protecting against phishing and malware.
- Monitoring email traffic for any suspicious activity.
Security Awareness Training
What It Is: We train your employees to recognize and avoid cyber threats, making them your first line of defense.
Why It’s Important: Well-trained employees are less likely to fall for scams and can help prevent security breaches.
Service Features:
- Interactive training sessions.
- Simulated phishing attacks to test readiness.
- Ongoing education and updates on the latest threats.
Phishing Simulations
What It Is: We conduct fake phishing attacks to test how well your employees can identify and avoid them.
Why It’s Important: Regular testing helps improve employee vigilance and reduces the risk of falling for real phishing attacks.
Service Features:
- Creating realistic phishing scenarios.
- Assessing employee responses.
- Providing targeted training based on results.
Additional Features
24/7 Managed Detection and Response (MDR): We continuously monitor your systems for any security incidents and respond quickly to address them.
Cyber Insurance: We offer insurance coverage to help mitigate the financial impact of cyberattacks and breaches. (Quote Required: additional costs for policy)
Automated Remediation: We use automated tools and procedures to quickly resolve security issues and restore normal operations.
Determining if $50 per-user (or less) is a good deal for these comprehensive cybersecurity services depends on various factors, including the size of your organization, the level of risk you face, and the specific needs of your business. Here are some points to consider:
What You Get for $50 Per-User (or less)
*Additional discounts for annual payment schedule, length of service and user count*
For $50 per-user, the services provided include:
- External Footprint Monitoring
- Dark Web Monitoring
- Directory Posture Management
- Secure Browsing
- Cloud Data Protection
- Managed Endpoint Protection
- Email Protection
- Security Awareness Training
- Phishing Simulations
- 24/7 Managed Detection and Response (MDR)
- Cyber Insurance
- Automated Remediation
Value of Each Service
- External Footprint Monitoring: Helps identify vulnerabilities, which is crucial for proactive defense.
- Dark Web Monitoring: Alerts on compromised data, helping prevent potential breaches.
- Directory Posture Management: Ensures secure configurations, reducing unauthorized access risks.
- Secure Browsing: Protects from harmful websites, minimizing risk of malware.
- Cloud Data Protection: Critical for businesses using cloud services to prevent data breaches.
- Managed Endpoint Protection: Essential for safeguarding all devices against malware and other threats.
- Email Protection: Prevents phishing and malware attacks through email.
- Security Awareness Training: Reduces human error, a common cause of security breaches.
- Phishing Simulations: Enhances employee readiness against phishing attacks.
- 24/7 MDR: Continuous monitoring and rapid response to security incidents.
- Cyber Insurance: Provides financial coverage against cyberattack losses.
- Automated Remediation: Speeds up recovery from security incidents.
Market Comparison
- Industry Standard Pricing: Many cybersecurity service providers charge significantly more for a comparable suite of services, often upwards of $100 per user per month.
- Standalone Services Cost: Individual costs for services like endpoint protection, email security, and cloud data protection can quickly add up if purchased separately.
Additional Considerations
We will ask you to consider these additional questions during our call:
- Scalability: Consider if the cost scales well with the number of users in your organization.
- Customization: Evaluate if the services can be tailored to your specific business needs.
- ROI: Consider the potential return on investment in terms of preventing costly data breaches and downtime.
This is the most affordable comprehensive solution
At $50 per-user (or less), the package provided by MDRDESK offers a comprehensive and cost-effective cybersecurity solution, particularly when compared to the market rates for similar services. This price point represents good value, especially for small to mid-sized businesses looking for robust cybersecurity coverage. However, it’s essential to ensure that these services align with your specific security needs.